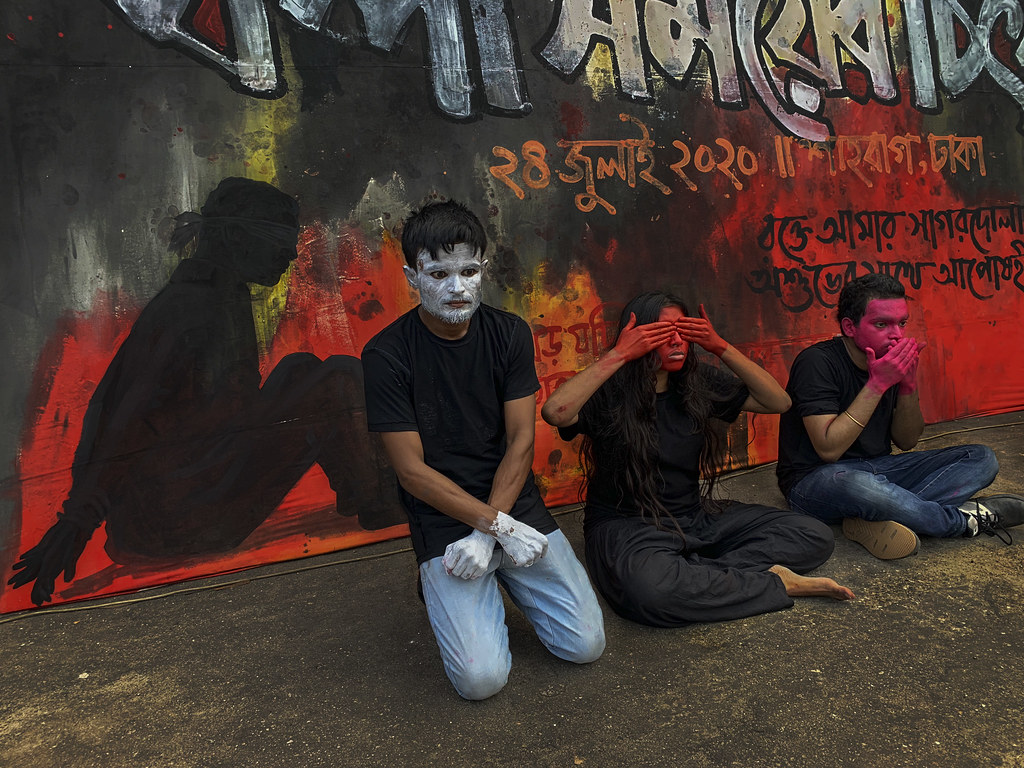Shahidul Alam is a Bangladeshi photojournalist, teacher, and social activist. A TIME “Person of the Year”, he is celebrated for his commitment to using his craft to preserve democracy in his country at all costs. See the project at http://mediastorm.com/clients/2019-icp-infinity-awards-shahidul-alam
Tag: surveillance
The Guardians: Time Magazine Person of the Year 2018

This year brought no shortage of other examples. Bangladeshi photographer Shahidul Alam was jailed for more than 100 days for making “false” and “provocative” statements after criticizing Prime Minister Sheikh Hasina in an interview about mass protests in Dhaka Continue reading “The Guardians: Time Magazine Person of the Year 2018”
Snooping on government snoopers
Hackers decide to turn their gaze on government. The Caravan
Are all telephone calls recorded and accessible to the US government?
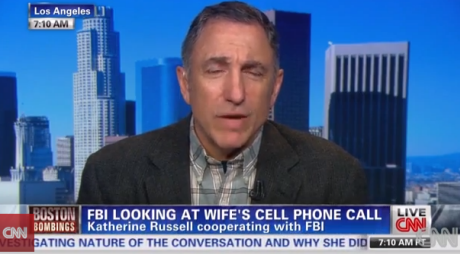
Your Wife Has Just Left the Country
Saudi Arabia Implements SMS–Tracking System
By?Kharunya Paramaguru?Nov. 24, 2012
?
HASSAN AMMAR / AFP / GETTY IMAGES?Saudi women have few travel choices: they either must take a taxi or have a male companion drive. But a new campaign encourages women to flout the ban.
Reports emerged of the system last week when?Manal al-Sherif, a women?s rights campaigner who has urged women to defy the driving ban, was alerted by a husband who received a message from the immigration authorities advising him that his wife had left the international airport in Riyadh. He happened to be traveling with her.
(MORE😕IKEA Edits Women Out of Saudi Arabian Catalog)
Women are treated as legal minors in the Saudi guardianship system, requiring permission from their male guardian if they want to work or study. Women who want to travel outside the country need their male guardian to sign what is known as a ?yellow sheet? at the airport or border.
Badriya al-Bishr a columnist critical of the Kingdom?s conservative interpretation of Islamic law,?said to the AFP?that women were being held under a ?state of slavery?,?adding?that ?this is technology used to serve backwardness in order to keep women imprisoned.?
The system notifying male guardians that their dependents?which includes their wife, children and foreign workers sponsored by them?had left the country appears to have been in place for a couple of years now.?Ahmed Al Omran, a Saudi blogger, explains that?it appears that this service, which in the past was an opt-out service, is now reaching those who had previously registered their details with the Ministry of Interior.
?The problem is not that there is now an electronic system that sends an SMS when women travel,??writes Omran. ?The problem is that the government is enforcing rules of male guardianships even on the rest of us who don?t believe in such rules.?
There are signs that the Kingdom is slowly changing its approach to the rights of women. Last year King Abdullah granted women the right to vote and run in the 2015 municipal elections. What impact that will have on the guardianship system however is yet to be determined.
The New Totalitarianism of Surveillance Technology
If you think that 24/7 tracking of citizens by biometric recognition systems is paranoid fantasy, just read the industry newsletters
by?Naomi Wolf

Yes, I know: it sounds like a paranoid rant.
Except that it?turned out to be true.?News21, supported by the Carnegie and Knight foundations, reports that Disney sites are indeed controlled by face-recognition technology, that the military is interested in the technology, and that the face-recognition contractor, Identix, has contracts with the US government ? for technology that identifies individuals in a crowd. Continue reading “The New Totalitarianism of Surveillance Technology”
Murdoch phone hacking scandal
Subscribe to ShahidulNews
Murdoch phone hacking scandal engulfs all Britain?s major parties
By Jean Shaoul
22 September 2010
World Socialist Website
A desperate damage control operation is underway as further allegations emerge about the extent of the illegal phone hacking at the Rupert Murdoch-owned?News of the World. The paper?s royal editor and a private investigator were found guilty of hacking into the voice mail of members of the Royal family and their aides in 2007.
It is now alleged that the practice was much more prevalent than was revealed at the time and that the Metropolitan Police failed to investigate all the cases known to them.
Journalist Clive Goodman and private investigator Glenn Mulcaire were found guilty at the Old Bailey in January 2007 after they admitted hacking into phones. Goodman was jailed for four months and Mulcaire for six months.News of the World editor Andy Coulson resigned following the case. He denied knowing about the hacking, but he accepted ultimate responsibility as editor of the paper. Prime Minister Gordon Brown immediately phoned to offer his commiserations. He assured the journalist that he had acted honourably in resigning and expressed his confidence that Coulson would soon have another job.
Coulson is now Prime Minister David Cameron?s director of communications and at the centre of the new allegations. His presence in the new Conservative/Liberal Democrat coalition administration implicates all three major political parties in the affair. It is now suggested that under the previous Labour government, the police and parliamentary investigations were cut short. The Liberal Democrats, who challenged Coulson?s claims that he was ignorant of the phone hacking, are now part of an administration in which Coulson plays a key role and must, as deputy Prime Minister Nick Clegg did in the House of Commons earlier this month, defend him.
A network of relationships has been exposed which reveal the incestuous nature of the British political elite and its ties to global corporate interests, in particular to Rupert Murdoch?s News International Corporation. A coalition government has just come to power that supposedly represents a new chapter in British political life after 13 years of Labour rule. But the Murdoch empire has slipped seamlessly from one government to the next. Even if Coulson is never charged with any crime and never found guilty of any crime, this affair will have demonstrated beyond a shadow of doubt that official politics in Britain is entirely divorced from the interests of ordinary people and in the hands of a criminal oligarchy who act outside the law.
Real political power lies with this plutocratic layer and not with elected representatives in Parliament. Allegations have emerged this month that the House of Commons Culture, Media and Sport Committee held back from pursuing its investigation into phone hacking at the?News of the World. Adam Price, a former Plaid Cymru MP who retired from Parliament in May, claims that MPs were afraid that their private lives would come under investigation if they called on News International Chief Executive Rebekah Brooks to testify. Members of the committee discussed getting the sergeant-at-arms to issue a subpoena for Mrs. Brooks.
Continue reading “Murdoch phone hacking scandal”
Photography is Not a Crime
Subscribe to ShahidulNews
Photography is Not a Crime
It?s a First Amendment Right
By Carlos Miller
The Homeland Security Bureau of the Miami-Dade Police Department has published a ?Terrorist Awareness Guide? where it advises citizens to be on the lookout for people taking ?inappropriate photographs or videos.?
And no, they are not talking about perverts shooting?up the skirts of women.
They?re talking about people taking photographs of surveillance cameras and other things that are plainly visible to the naked eye.
Here is an excerpt of what the pamphlet says:
Maybe you are at a National Monument and you
notice a person nearby taking a lot of photos. Not
unusual. But then you notice that he is only taking
photos of t he surveillance cameras, crash barriers at
the entrances, and access control procedures. Is that
normal for a tourist? Absolute not!
The following should cause a heightened sense of
concern:
??????? Unusual interest
??????? Surveillance
??????? Inappropriate photographs or videos
??????? Note-taking
??????? Drawing of diagrams
??????? Annotating maps
??????? Using binoculars or night vision devices
It should be noted that Detective Bustamante of the same homeland security bureau was one of the officers who responded to our?first Metrorail incident where we were ?permanently banned? for taking photos.
Bustamante proved pretty clueless of the law when he informed us we needed a permit to photograph anything within the Metrorail, regardless if we were shooting commercial or not.
Read the entire document below. The portion on photography is on the second page in the right-hand column circled in red.
Terrorist Awareness Guide MDPD-PINAC

National ID Cards: In the Interest of Surveillance?
by rahnuma ahmed
Official: ?You ought to have some papers to show who you are.?
Protagonist: ?I do not need any papers. I know who I am.?
Official: ?Maybe so. But others are also interested in who you are.?
— Kafkaesque journey of American sailor who has lost his identity papers, B. Traven, The Death Ship (tr. 1934)
A non-fraudulent voter list, `a priceless gift to the nation’
Praise was due. And it was given.
Ms Renata Dessallien, UN Resident Coordinator and UNDP Resident Representative, at a function marking the celebration of the successful completion of voter registration, organised by the Election Commission on July 22, spoke of it in glowing terms. It was “a truly historic achievement,” because never before “have so many people been electronically registered in such a short time” in any other country in the world. What was impressive was the immense scale of the undertaking, the accuracy of the list, the elimination of duplicate and fraudulent entries. “If there were a Nobel Prize for voter lists, Bangladesh would be the clear winner!”
The Chief Advisor Dr Fakhruddin Ahmed termed it a “milestone,” one that would enable not only the upcoming elections to be “free, fair and credible” but also, future ones, by setting high standards. The Chief Election Commissioner ATM Shamsul Huda, called it a “memorable event in the annals of country’s history.” At an earlier event, “Celebrating the Halfway Mark of Voter Registration” held in early March, the Chief of Army Staff General Moen U Ahmed had voiced hopes that it would “lay the foundation for building a meaningful democracy.”
A similar nationwide voter registration venture had failed in 1997 because the names and pictures of most people did not match, and many had failed to turn up to register at the appointed time. The nation, as a result, had been Tk 115 crore poorer. A proposed integrated project of Machine Readable Passports (MRP) and National Identity Cards (NID) in 2005 had been budgeted at Tk 1,400 crore. Its completion would take 5 years, the first year would be a “test” period. The 2006 voter list, prepared by the past EEC Justice MA Aziz for the 2007 elections had been faulty, it had registered an excess of 1.2 crore voters, leading to a political impasse that helped usher in the current military-backed Fakhruddin government.
In comparison to all previous efforts, the current effort has yielded a faultless voter list, one that is computerised, consisting of a data-base of 80 million 500 thousand 723 voters with photographs and fingerprints. It has cost only Tk 424 crore, one-third of the 2005 estimate, and has been successfully completed in a mere 11 months. The Election Commission was the sponsor and the coordinating agency, the Bangladesh army was the operational agency. Together they coordinated the huge logistics in a “very tight time frame”, as Major General Shafiqul Islam, Military Secretary, Bangladesh Army, said in an interview to find Biometrics, `we required 12,000 laptops to be deployed throughout the country, 8,000 printers, paper, toner, train a staff of 18,000 computer and enrollment personnel, in a situation where on an average data was collected on 300,000 to 400,000 people daily.’ The resulting electoral rolls, perhaps one of the largest electronic databases in the world, will definitely be the largest among developing countries.
A survey of the voter registration process funded by the UK Department for International Development (DFID) announced it to be of international standard, in the words of one of the consultants, “a list of quality no less than that of America or England.” The UN is said to be considering replicating this model in other developing countries.
The current voter list, as one of the national English dailies commented in its editorial, is “a priceless gift to the nation.”
The National ID Card, `an offshoot’
The EC project was titled the Preparation of Electoral Roll with Photographs and Facilitating the Issuance of National Identity (ID) Card. In the words of Mike DePasquale, Chief Executive Officer of BIO-Key International Inc, a US-based company which is a leader in finger-based biometric identification and wireless public safety, the NID was “an offshoot” of the voter registration project — a “co-operative venture” between BIO-Key in the US, Tiger IT in Bangladesh, and the Bangladesh army.
Brigadier General (Retired) Shahedul Anam Khan, a defence analyst, thinks the government did well to undertake both projects simultaneously. Up to a stage, “the modalities involved for the preparation of both” like basic data collection and cross checking, are similar. The ID Card was a “spin-off,” which, if it had been put off for later, would have cost more.
But, for people on the ground, the two were not as separable. M Sakhawat Hussain, one of the Election Commissioners, puts it in words closer to how we, as potential voters, experienced it, “No one will be listed as a voter without the registration of the name on the electoral roll and no one will get the national ID card.”
Advocates of e-government are also advocates of national ID cards, for instance Farooq Sobhan, M. Shafiullah and others write in a Study of eGovernment in Bangladesh (Bangladesh Enterprise Institute, April 2004), “Bangladesh should take active steps to initiate a project for national ID” because it will provide an important base for the provision of eGovernment services “efficiently and in a personalized way,” to citizens who will have unique ID numbers. I came across several Bangladeshi bloggers who seemed to hold similar views. According to one, it would be “a solution to many problems,” a national database would hold information from voter lists to tax records, it would make easier many tasks from machine-readable passports to criminal investigations. According to another, the digitisation of national-level information would make governance procedures “more scientific.”
The EC has drafted an ordinance making national ID cards mandatory for citizens, ?for getting any services from the government, its departments and institutions or from any statutory government offices.’ Twenty two services are listed, these include the issuance and renewal of passport, driving licence, trade licence, tax identification number, business identification number and bank account. It also states that nobody will get government subsidy facilities, allowance and relief if they do not have identity cards. Very recently, the council of advisors approved the formation of the National Identity Registration Authority Ordinance 2008. It authorises the home ministry to provide national ID cards. Under the proposed ordinance, the EC will hand over all information that has been collected — data and biometric features of the citizens — to NIRA, a statutory body. The ordinance declares false information, forgery, having more than one ID card a criminal offence, punishable by three months to seven years rigorous imprisonment, along with monetary fines.
That confusion exists among people in general — the beneficiaries of the national ID card — was revealed during the four city corporation and nine pouroshobha elections held recently. Voters had come to the polling centres with their national ID cards, and were confused over why the serial number of their ID cards did not tally with the voter serial numbers. This resulted in delays in vote casting, and in long queues. Voter identity cards had been given in the 90s, or torn-off slips containing registration numbers, and as a newspaper report states, during the recently-held local-level elections, the common perception had been that the `ID card was to be used for voting purposes.’ Reports say, polling officers had been similarly confused. M Shakhawat Hossain, Election Commissioner, blamed the media for publicising what in effect was a `national ID card’, as a `voter ID card’, even though, according to him, the EC had carried out a huge campaign to clarify the differences between the two.
The ‘largest biometric database in the world’
What is less public knowledge is that the four fingerprints of each voter that was captured with BIO-key’s fingerprint ID software, and FBI-certified fingerprint readers, has already generated over 300 Million ISO fingerprint templates. Combined with the 400 million projected to be generated, it will become by far the largest biometric deployment in the world.
Duplicate registrations are being accurately identified says Ziaur Rahman, Managing Director of Tiger IT BD Ltd. (Tiger IT), a company that is a leader in both prepackaged and customized software solutions and was BIO-Key’s “systems integrator on the ground,” at a speed of “one million matches per second on a single processor.” Tiger IT Bangladesh’s website provides further information on the national ID card (by the way, the domain tigeritbd.com was registered as recently as August 2007). The card includes a standard barcode which is encoded with ISO fingerprint templates, and PKI digital hash. These can be used to quickly verify the identity of the cardholder while ensuring the integrity and authenticity of the ID card. The Cognitec Facial Recognition Software has been used to capture facial images.
While Renata Dessallien enthuses over how “modern technology” enables the prevention of vote theft, and DePasquale prides on how BIO-Key’s patented technology is “performing better than anything else in the market for finger matching,” I have simple questions to ask: who owns my fingerprints? how will it be used? can NIRA transfer it to government departments within Bangladesh without my knowledge? or, maybe even outside the country’s borders? As the British government did when it passed more than 500 samples of DNA to foreign agencies, but when asked “no one seemed to know” to which countries.
The European Comission recently proposed the harmonisation of security features on passports across the European Union. The proposal, introduced in October 2007, requires Member States to take measures to introduce biometric features, including fingerprinting, on passports and travel documents. The fingerprints would be stored in a centralised database. The European Union Data Protection Supervisor, Peter Hustinx, who is in charge of safeguarding the personal data and the right to privacy of EU citizens, has expressed his concern since it fails to “adequately safeguard the right to privacy of EU citizens.” He says, the Commission failed to consult with his office prior to submitting the proposal, as required by EU law.
The current regime’s voter registration list has, in all probability, lessened the likelihood of fraudulent votes. But it also has, in all likelihood, laid the groundwork for installing a new regime of surveillance, one that will be deployed against the citizens of Bangladesh.
First published in New Age on Monday the 29th September 2009
Insecure at last: the age of surveillance
Subscribe to ShahidulNews
By Rahnuma Ahmed
 |
?I am worried about this word, this notion ? security. I see this word, hear this word, feel this word everywhere. Security check. Security watch. Security clearance. Why has all this focus on security made me feel so much more insecure??
? Eve Ensler, ?Insecure at Last: A Political Memoir.?
Tailor-made, to suit your needs
Surveillance often works innocuously. Consider this: billboards equipped with small cameras that gather details about passers-by ? gender, a rough estimation of age, and how long she or he looks at the billboard. The cameras, it is said, use software to establish that the person is a billboard-viewer, it then analyses her or his facial features like cheekbone height, distance between nose and chin, to judge the person?s gender and age. Race is not used as a parameter. Not yet, but the companies say that they can, that they will. These details are transmitted to a central database. The purpose is to ?tailor? a digital display of the viewer, ?to show one advertisement to a middle-aged white woman,? and another to ?a teenage Asian boy.? To sell products more efficiently. More rationally. It does not intrude on privacy, so the argument goes, since actual images of billboard viewers are not stored.
These billboards are similar to websites such as Amazon, described as the largest (virtual) bookstore in the world, tailor-made to assist the customer, her needs and interests. I visit the website to look up books on feminist theory, I am shown bell hooks? Feminist Theory: From Margin to Centre, along with, Ain?t I a Woman: Black Women and Feminism, also written by her, one that is, so I am told, ?Frequently Bought Together.? Simultaneously, five other products are displayed, that Customers Who Bought This Item Also Bought. Down below are menus which, at a click, will display my Recent History, books recently purchased, or viewed by me.
The Surveillance Society
Surveillance, as a growing number of Western writers, journalists, artists, academics and human rights activists keep reminding us, is no longer ?the future?. In the words of Henry Potter, London editor of Vanity Fair, ?we are already at the gates of the surveillance society.? According to a group of academics, writers of A Report on the Surveillance Society (September 2006), it exists ?not merely from dawn to dusk,? but for twentyfour hours a day, seven days a week. It is systemic, expressed not only through supermarket check-out clerks who want to see loyalty cards, or the coded access card that allows one to enter the office, or CCTV (closed-circuit TV) cameras, which in Britain, are ?everywhere.? A CCTV consulting firm puts the number deployed at more than 4 million, nearly as many as the rest of the world combined, minus the United States. The report?s authors write, ?these systems represent a basic, complex infrastructure which assumes that gathering and processing personal data is vital to contemporary living.? Surveillance is,?in their words, a ?part of the fabric of daily life.?
They write, it would be a mistake to think of surveillance as ?something sinister, smacking of dictators and totalitarianism,? or as ?a covert conspiracy.? Instead, it is the outcome of modern organisational practices, business, government and the military. It is better viewed as the progress towards efficient administration, as a benefit for the development of Western capitalism and the modern nation-state. Four hundred years ago, rational methods began to be applied to organisational practices, to ensure that the new organisations ran smoothly. It made informal social controls on business and governing, and people?s ordinary social ties ?irrelevant.? The growth of new computer systems after World War II reduced labour intensity, it increased the reliability and the volume of work that could be accomplished. Subsequent growth of the new communications system, now known together as ?information technology? (IT), is related to modern desires for efficiency, speed, control and coordination, and is global.
Capitalism?s push to cut down on costs and to increase profits has accelerated and reinforced surveillance. This, accompanied by the 20th century?s growth of military and police departments, and the development of new technologies, has improved techniques of intelligence-gathering, identification and tracking. Surveillance thus, has become part of being modern.
It is undoubtedly two-sided. It has its benefits: it helps deter traffic violations, tracks down criminals, medical surveillance programmes provide necessary information to public health authorities etc. But, the authors warn us, there are things that are ?seriously wrong? with a surveillance society. Large scale technological infrastructures suffer from problems, equally large in scale, especially computer systems where a mistaken, or an imprudent keystroke can cause havoc. For instance, twenty million ordinary peoples? online search queries from AOL were released for ?research? purposes in August 2006. The names of identifiers were not tagged, but connecting search records with names took only a couple of minutes. Corruptions and skewed visions of power, not that of tyrants, but of leaders justifying extraordinary tactics in exceptional cicumstances, such as the endless ?war on terror,? can be disastrous. Many Muslim Americans have been branded as unfit for travel, or subject to racial profiling. Surveillance systems are wrong on three other counts: they are `meant to discriminate between one group and another?, as recent trends show, distinctions of class, race, gender, geography and citizenship are being exacerbated and institutionalised. Second, it undermines trust, something necessary to social relationships, breeding suspicion in its place. When parents start to use webcams and GPS systems to check on teenage childrens? activities, or spouses check each others? suspected infidelities, it speaks of a ?slow social suicide.? And third, surveillance systems associated with high technology and anti-terrorism distract us from pursuing ?alternatives,? from paying attention to larger and more urgent questions.
Fear internalised
Caroline Osella, a contributor to the ASA (Association of Social Anthropologists) blog discussion on recruiting anthropologists in the ?war on terror? (through the Human Terrain System programme), wrote of a personal experience that illustrates the ?state of paranoid anxiety? that grips people. As the mother of an 11 year-old, she had gone to a school meeting for parents to discuss a planned residential adventure school trip. She was astounded, she writes, to see parents not asking questions about activities planned, or practicalities like food, or other stuff to take along. Instead, questions revolved exclusively around security. School authorities were asked: ?will an adult stay awake all night to monitor that kids are safe and not wandering?,? ?can the kids escape to the outside?,? ?can strangers get in?? And she writes, incredible as it may sound, one father finally asked, ?what guarantee can the school provide that paedophiles will not be able to break the perimeter fence and get into the site, where the kids will be sleeping unchaperoned in tents??
It was surreal, Osella writes, to sit and listen to ?reasoned and careful discussions? of a totally fantastic scenario. It would be great, she says, to embrace some insecurity and uncertainty, and to accept the absence of ?total control? over our lives.
How does surveillance get naturalised? Mark Andrejevic, author of Reality TV: The Work of Being Watched, believes that reality TV has played a part in transforming American attitudes toward surveillance. Producers of early reality programs such as MTV?s The Real World (1992) had a hard time finding people willing to have their lives taped nearly 24 hours a day for several months. Now, thousands of young people form audition lines in college towns, ?more people applying to The Real World each year than to Harvard.? New generations, Andrejevic says, are growing up viewing television shows that let anyone see the lives of others recorded voluntarily. There are other reality shows too, like COPS, where police chases of criminals is filmed. Increasingly, he says, the results of surveillance are seen as `entertainment,? as being within the realm of the public?s right to know.
The mass collection of DNA data, and ?policy? laundering
The introduction of the Serious Organised Crime and Police Act 2005 in the UK has led to anyone being arrested on ?suspicion? of committing the slightest offence. After arrest, the police remove a DNA sample, which stays on the police database, even though the person may not be charged. Increasing by 40,000 samples per month, the database has surpassed more than 3 million DNA samples, a fifth of which belong to people of African-Caribbean origin. Who owns these DNA samples? ?Once a database like this is established, the authority concerned tends to regard the information as being in its ownership, to be exchanged without reference to the subjects,? writes Potter. The British government admitted that it had passed more than 500 DNA samples (I wonder whose, Arabs? Muslims?) to foreign agencies. But when asked to which countries, ?no one seemed to know.? The chairman of the Nuffield Bioethics Committee, Sir Bob Hepple anxiously commented, ?We didn?t have any legislation to establish the DNA database and it has not been debated in parliament.?
Western governments, it seems are devising new strategies to circumvent traditional ideals of civic liberty, based on notions of freedom and privacy (mind you, not in its colonies). Dr Gus Hosein, senior fellow with Privacy International says, ?illiberal policies? are pushed through international treaty organisations. The British government brought into effect communications surveillance policies through the European Union, and ID cards through the United Nations. ?The government returns home to Parliament, holding their hands up saying ?We are obliged to act because of international obligations? and gets what they want with little debate.? It is a strategy that has led to the coinage of new words: ?policy laundering.?
Having originated in the West, these surveillance systems are gradually extending outside it, to control, regulate and limit the lives of people in non-Western countries.
First published in The New Age on 15th September 2008